Security testing tools are performed with the intention of revealing flaws in security mechanisms and finding the vulnerabilities or weaknesses of software applications. These tools are pivotal in a company’s business strategy. As crucial as software testing is, and as beneficial as software testing tools are, the implementation process is highly customized to suit the need of the business. For this reason, it is important to have a trusted software security testing vendor.
According to Annual Cybersecurity Report, over 33% of the organizations all over the globe had to deal with a cyber-breach in 2016. This resulted in a severe loss of users, business opportunities and overall revenue by a whopping 20%. The report surveyed nearly 3,000 chief security officers (CSOs) and security operations leaders from 13 countries.
This is the most advanced and popular Framework that can be used to for pen-testing. It is based on the concept of ‘exploit’ which is a code that can surpass the security measures and enter a certain system. If entered, it runs a ‘payload’, a code that performs operations on a target machine, thus creating a perfect framework for penetration testing.
It can be used on web applications, networks, servers etc. It has a command-line and the GUI clickable interface works on Linux, Apple Mac OS X and Microsoft Windows.
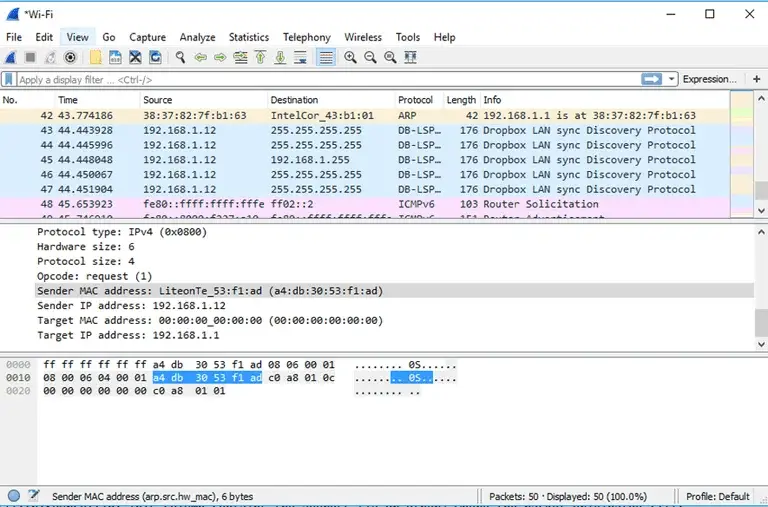
This is basically a network protocol analyzer –popular for providing the minutest details about your network protocols, packet information, decryption etc. It can be used on Windows, Linux, OS X, Solaris, FreeBSD, NetBSD, and many other systems. The information that is retrieved via this tool can be viewed through a GUI or the TTY-mode TShark utility.
Kali Linux is an open source project that is maintained by Offensive Security.Few prime features of Kali Linux include Accessibility, Full Customization of Kali ISOs, Live USB with Multiple Persistence Stores, Full Disk Encryption, Running on Android, Disk Encryption on Raspberry Pi 2, etc.
Tools Listings, Metapackages, and version Tracking are some of the Penetration Testing tools present in Kali Linux.
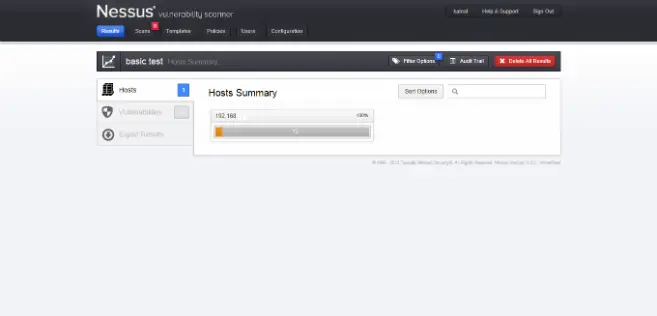
Nessus is also a scanner and it needs to be watched out for. It is one of the most robust vulnerability identifier tools available. It specializes in compliance checks, Sensitive data searches, IPs scan, website scanning etc. and aids in finding the ‘weak-spots’. It works best on most of the environments.
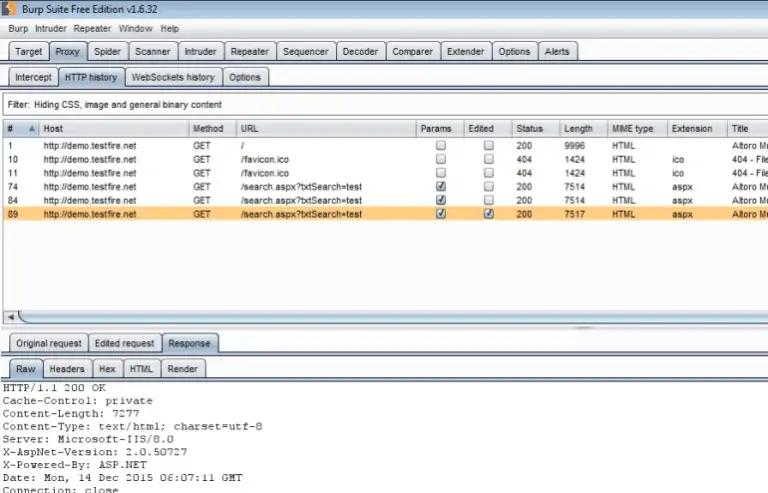
Burp suite is also essentially a scanner (with a limited “intruder” tool for attacks), although many security testing specialists swear that pen-testing without this tool is unimaginable. The tool is not free, but very cost effective. Take a look at it on the below download page. It mainly works wonders with intercepting proxy, crawling content and functionality, web application scanning etc. You can use this on Windows, Mac OS X and Linux environments.
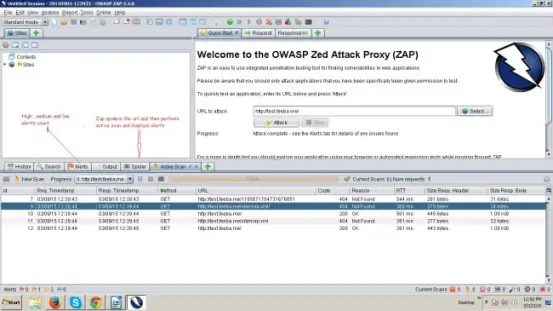
ZAP is a completely free to use, scanner and security vulnerability finder for web applications. ZAP includes Proxy intercepting aspects, a variety of scanners, spiders etc. It works best on most platforms.
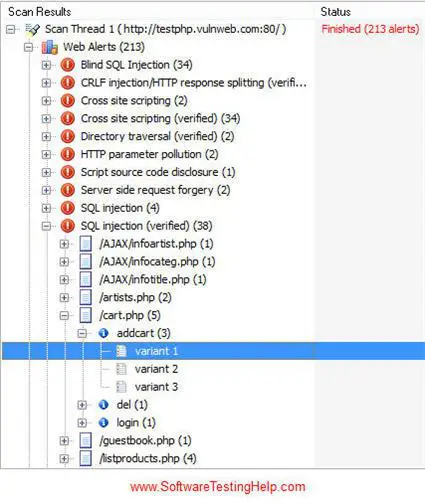
Acunetix is essentially a web vulnerability scanner targeted at web applications. It provides SQL injection, cross-site script testing, PCI compliance reports etc. along with identifying a multitude of vulnerabilities.
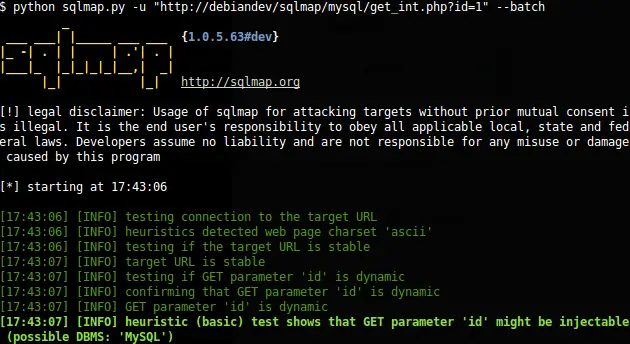
Sqlmap is again a good open source pe-testing tool. This tool is mainly used for detecting and exploiting SQL injection issues in an application and hacking over of database servers. It comes with the command-line interface. Platform: Linux, Apple Mac OS X, and Microsoft Windows are its supported platforms. All versions of this tool are free for download.
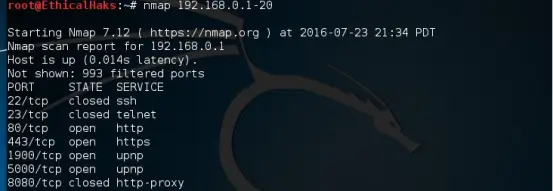
“Network Mapper” though not necessarily a pen-testing tool, it is a must-have tool for the ethical hackers. This is a very popular tool that predominantly aids in understanding the characteristics of any target network. The characteristics include host, services, OS, packet filters/firewalls etc. It works on most of the environments and is open sourced.
Security testing is the most important part of an application and checks whether confidential data stays confidential. In this type of testing, tester plays a role of the attacker and play around the system to find security-related bugs. This security testing is very important in IT industry to protect data by all means.
For more information about Security Testing Tools and Services, Contact us today.