As businesses increasingly rely on Cloud Integration Platforms like Boomi to streamline operations and connect disparate systems. Ensuring the security of Boomi integrations becomes paramount in today’s rapidly evolving digital landscape. This blog post explores the essential best practices and tools for effectively securing Boomi integrations, implementing Boomi security to protect sensitive information, mitigating risks, and ensuring the seamless functioning of integrated systems in any business ecosystem.
To secure Boomi integrations, a comprehensive approach is needed, covering authentication, encryption, and network security. Let’s delve into each of these areas to uncover the available best practices and tools.
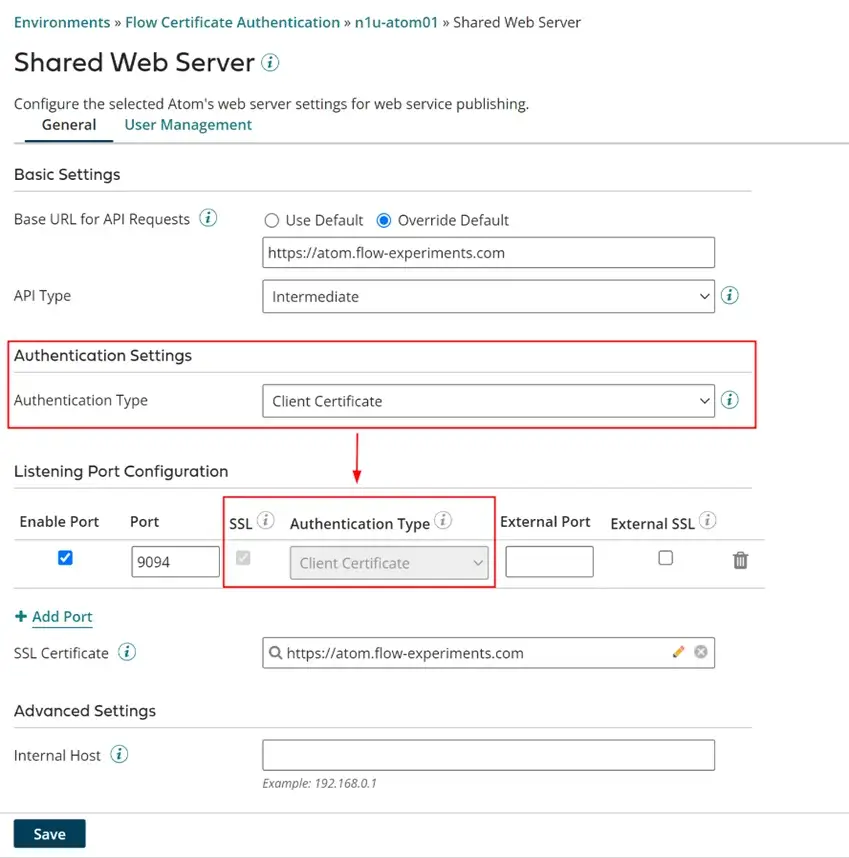
1. Authentication Best Practices
Authentication is a crucial aspect of securing Boomi integrations, serving as the primary defense. With Boomi security iPaaS tool, organizations can implement robust authentication mechanisms to verify user identities and prevent unauthorized access. Boomi offers various authentication options, including username/password, SAML, OAuth, and API keys, making it one of the best IPaaS software solutions for authentication in data integration scenarios. The choice of authentication method depends on the specific integration requirements and desired security level. To ensure secure Boomi integrations, it is essential to adhere to authentication best practices, such as enforcing strong password policies, implementing multi-factor authentication when appropriate, and securely managing authentication credentials.
1.1 Importance of authentication in securing integrations
Authentication is a critical component of securing Boomi integrations. It ensures that only authorized users or systems can access the integrated applications and data. By verifying the identity of users or systems, authentication prevents unauthorized access, data breaches, and potential security threats. Strong authentication measures are essential to protect sensitive information and maintain the integrity of the integration ecosystem.
1.2 Available authentication methods in Boomi (username/password, SAML, OAuth, API keys)
Boomi offers several authentication methods to accommodate different integration scenarios and security requirements. These authentication methods include:
1.2.1 Username/Password: The traditional username and password authentication is widely used and provides a basic level of security. It is suitable for integrations where simplicity and ease of use are the primary considerations.
1.2.2 SAML (Security Assertion Markup Language): SAML-based authentication allows for single sign-on (SSO) capabilities and seamless integration with identity providers. It enables users to authenticate once and gain access to multiple integrated applications without the need for separate credentials.
1.2.3 OAuth (Open Authorization): OAuth is commonly used for API integrations and allows delegated access to resources. It provides a secure and standardized way for applications to grant access to data or perform actions on behalf of users, without sharing their credentials.
1.2.4 API Keys: API keys are unique identifiers that applications use to authenticate themselves when making API requests. They are often used for machine-to-machine authentication, ensuring secure communication between systems.
1.3 Guidelines for selecting the appropriate authentication method based on integration scenarios
When selecting the authentication method for Boomi integrations, consider the following guidelines:
1.3.1 Security Requirements: Evaluating the sensitivity of the data being transmitted and the level of security required. Higher-security integrations may require stronger authentication methods, such as SAML or OAuth, while less sensitive integrations may use username/password authentication.
1.3.2 Integration Type: Considering the type of integration being performed. If the integration involves multiple applications and users, SAML-based SSO may provide a seamless and secure authentication experience. For API integrations, OAuth or API key authentication may be more suitable.
1.3.3 Compatibility: Ensuring that the authentication method chosen is compatible with the applications and systems being integrated. Some systems may only support specific authentication protocols, so compatibility is crucial for successful integration.
1.3.4 User Experience: Considering the user experience and ease of use when selecting an authentication method. Complicated or cumbersome authentication processes may lead to user frustration and potentially impact productivity.
1.4 Best practices for managing and securing authentication credentials
To effectively manage and secure authentication credentials in an iPaaS tool like Boomi, follow these authentication best practices for Boomi integration security:
1.4.1 Strong Password Policies: Enforcing strong passwords, complexity, and expiration periods.
1.4.2 Secure Credential Storage: Using encryption or hashing to protect sensitive information.
1.4.3 Role-Based Access Controls: Defining user roles and restrict access to sensitive integration components.
1.4.4 Regular Credential Reviews: Periodically reviewing and revoking access for inactive or unnecessary accounts.
1.4.5 Multi-Factor Authentication (MFA): Implementation of MFA to add an extra layer of security.
1.4.6 Secure Key Management: Following industry standards for generating, storing, and rotating cryptographic keys.
1.4.7 Regular Auditing and Monitoring: Implementation of auditing and monitoring capabilities to track authentication activities.
1.4.8 User Education and Awareness: Educating users on best practices, password protection, and recognizing phishing attempts.
Implementing these authentication best practices in Boomi, an iPaaS data integration tool, enhances security and reduces the risk of unauthorized access and potential breaches.
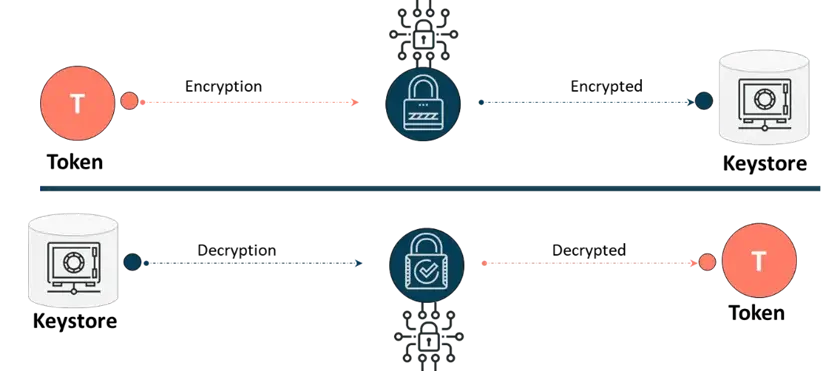
2. Encryption and Data Protection
Boomi, as one of the best iPaaS software solutions, follows industry-leading best practices for cloud data encryption and integration security. Encryption is a fundamental aspect of Boomi’s data protection strategy, providing confidentiality and integrity during data transmission and storage.
Boomi leverages Secure Socket Layer (SSL) or Transport Layer Security (TLS) protocols to encrypt data while it’s in transit. These protocols establish a secure communication channel between systems, ensuring that sensitive information remains encrypted and protected from unauthorized interception.
Furthermore, Boomi emphasizes encryption at rest to safeguard data stored within its platform and associated components. This approach ensures that even if unauthorized access occurs, the data remains encrypted and inaccessible without proper decryption keys.
To implement encryption effectively, Boomi adheres to best practices, such as employing strong encryption algorithms, carefully managing encryption keys, and utilizing secure key storage mechanisms. These measures help maintain the confidentiality and integrity of data throughout the integration process.
2.1 Encryption during Transit
Boomi supports SSL/TLS encryption to secure data during transmission between systems. It establishes encrypted connections, preventing unauthorized access to sensitive information. Implementing SSL/TLS in Boomi involves configuring certificates for connectors or endpoints, ensuring data confidentiality and protection against eavesdropping.
2.2 Encryption at Rest
Boomi security tools enable encryption at rest, securing data stored within its platform. It utilizes underlying storage technologies that support encryption to safeguard sensitive information. Encrypting data at rest ensures that even if unauthorized access occurs, the encrypted data remains protected without the decryption key.
2.3 Encryption of Sensitive Data within Processes
Boomi offers encryption capabilities within integration processes to secure sensitive data. It provides encryption shapes and supports algorithms like AES to encrypt and decrypt specific data fields. This protects personally identifiable information, financial data, and passwords within integration workflows, reducing the risk of unauthorized access or data exposure.
3. Network Security
Securing network connectivity is vital for protecting Boomi integrations and ensuring the overall security of the Dell Boomi iPaaS platform. Implementing robust network security measures and following best practices is essential. Here are some key network security practices for securing Boomi integrations:
3.1 Firewall Configurations
Setting up firewall rules helps to control inbound and outbound traffic, allowing only necessary connections and blocking unauthorized access. Regularly review and update firewall configurations to align with security requirements.
3.2 IP Whitelisting
Restricting access to Boomi integrations by implementing IP whitelisting. Only trusted sources with approved IP addresses should be allowed to connect to the Boomi platform.
3.3 Virtual Private Networks (VPNs)
Establishing secure connections between systems using VPNs. This provides an additional layer of encryption and ensures secure communication between endpoints.
3.4 Secure Protocols
Utilizing secure protocols like HTTPS and SFTP for encrypted data transmission. These protocols ensure data confidentiality and integrity during transit.
3.5 Monitoring and Logging
Implementation of monitoring and logging mechanisms within Boomi to track network activities and detect any suspicious behavior or potential security incidents. Regularly review logs to identify and respond to security events promptly.
3.6 Regular Security Updates
Keeping the Boomi platform and associated network components up to date with the latest security patches and updates. This helps address any known vulnerabilities and strengthens overall security.
Conclusion
Securing Boomi integrations is of utmost importance in the modern digital landscape, where businesses heavily rely on cloud integration platforms like Boomi. OdiTek understands the criticality of Boomi security and offers comprehensive services to ensure the protection of sensitive information, mitigate risks, and enable the seamless functioning of integrated systems.
Our team of experts follows industry best practices and utilizes cutting-edge tools to implement robust security measures for Boomi integrations. From authentication to encryption and network security, we provide a holistic approach to safeguarding your data and ensuring the integrity of your integration processes.







