Technical Impact & Business implication of Android App Reverse Engineering
Technical Impact
An attacker could use reverse engineering to hack your android application. Here are some important assets they can get access to:
1. They can reveal backend server information
2. Attacks on backend systems can be carried out
3. Can obtain the data required to make the last code changes
4. Intellectual property can be stolen using this method
Business Implications
Reverse engineering refers to the process of taking apart a product, device or system to understand how it works and how it was made. It has several business implications, including:
1. Theft of personal information
2. Identify theft threatens your reputation
3. Backend systems compromise
4. Copycat apps
5. Security vulnerabilities
6. Performance optimization
7. Compliance with regulation
How to Prevent Android Application from Reverse Engineering?
Android App reverse engineering prevention is challenging, but there are several steps that businesses can take to minimize the risk of their apps being reverse-engineered. Here are some of the steps that businesses can take to prevent Android App reverse engineering:
1. Obfuscation
Obfuscation is the process of modifying the code to make it more difficult to understand. It can be used to change the names of classes, methods, and variables, as well as remove unused code. This makes it harder for attackers to understand the app’s functionality and logic.
2. Code encryption
Code encryption involves converting the code into a format that is not easily readable, making it more difficult to reverse engineer. Encryption can be applied to the entire code or specific parts of it that contain sensitive information.
3. Binary protection
Binary protection tools can be used to protect the app’s binary code from reverse engineering. These tools use various techniques such as code obfuscation, code virtualization, and anti-tampering measures to make the binary code more difficult to understand.
4. Root detection
Android devices that are rooted or jailbroken are more vulnerable to reverse engineering. By implementing root detection, businesses can prevent their app from being installed on rooted devices, reducing the risk of reverse engineering.
5. Server-side processing
Some business logic can be moved from the app to the server-side, where it is more difficult to reverse engineer. This approach can also improve the app’s performance and scalability.
6. Continuous monitoring
Regularly monitoring the app for any signs of reverse engineering can help detect and prevent attacks before they cause any damage. This can involve using tools that analyze the app’s behavior and network traffic to identify any suspicious activity.
In summary, preventing reverse engineering in Android apps requires a multi-faceted approach that includes code obfuscation, encryption, binary protection, root detection, server-side processing, and continuous monitoring. By implementing these measures, businesses can reduce the risk of their apps being reverse-engineered and protect their intellectual property, data, and reputation.
ProGuard
1. Best cross-platform open-source tool, which was created for to secure mobile apps in addition of shrinks, improves, obfuscate and check codes before running it.
2. Always make sure you have enabled ProGuard on your apps. ProGuard obfuscates your code making it difficult for hackers trying to break your app. You can do this by simply enabling the following options in your app/build.gradle file
How to use ProGuard in Native Android Application?
1. In Android Studio, open application and go to Gradle Scripts -> build.gradle(Module).
2. Add below lines inside release:
debuggable false
minifyEnabled true
shrinkResouces true
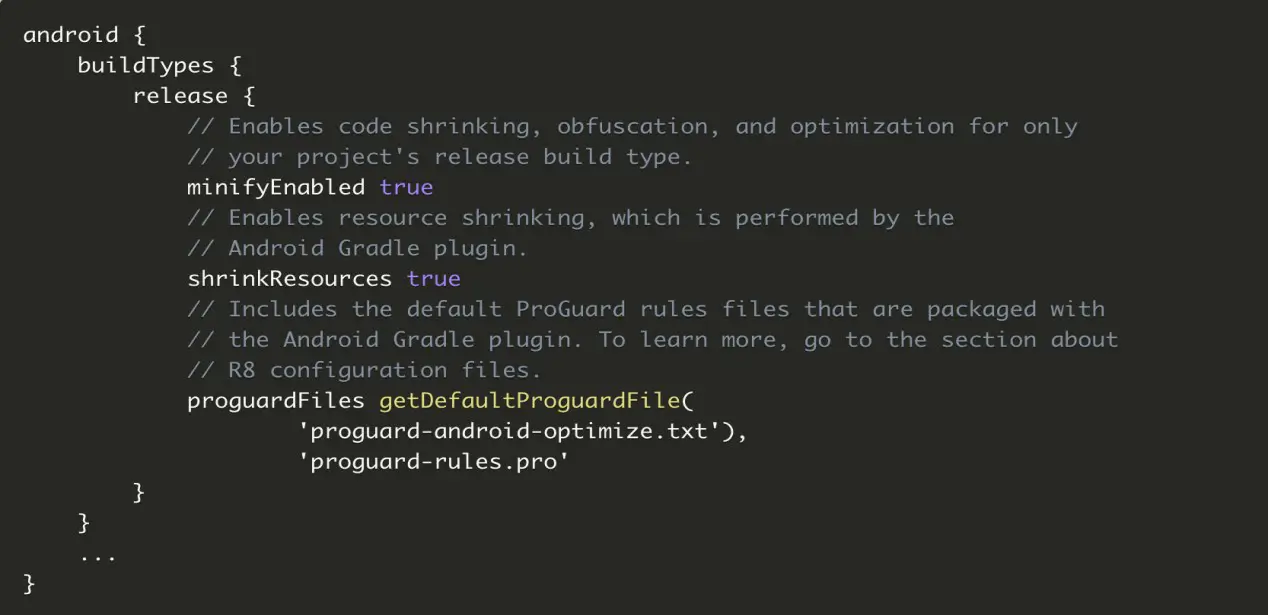
3. Here in code, you can see the file named ‘proguard-android-optimize.txt’ which is a file generated by android which includes some set of rules. If we want to change or include rules to keep safe android apps.
4. Simply open the file named ‘proguard-rules.pro’ and add any rules which is implies to your app.
Primarily code as:
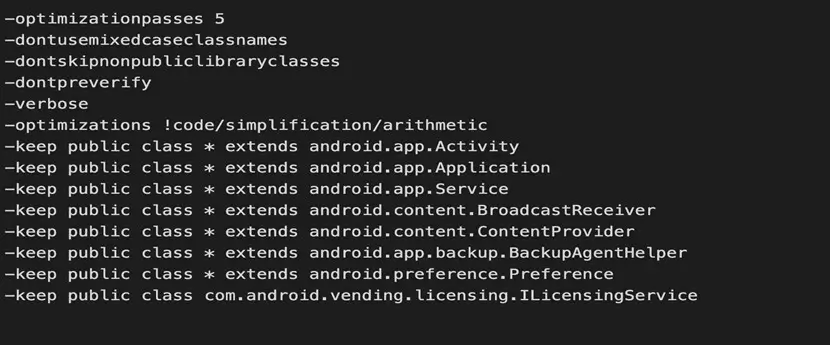
5. Similarly we can add other libraries proguard rules those we are using in our application.
How to use ProGuard in Hybrid Android Application?
IONIC Application
1. Install the Cordova ProGuard plugin by running the following command in your ionic project terminal:

This plugin enables ProGuard for your Cordova project.
2. In your Ionic project directory, open the ‘config.xml’ file and add the following line inside the ‘
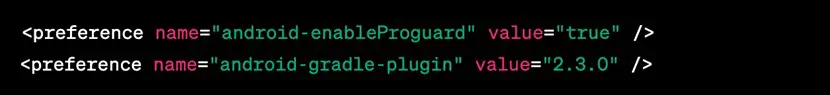
3. Then create a file named ‘proguard-android.txt’ inside platform-> android
4. Open ‘build.gradle’ inside platform -> android -> app folder.
5. Add below code:
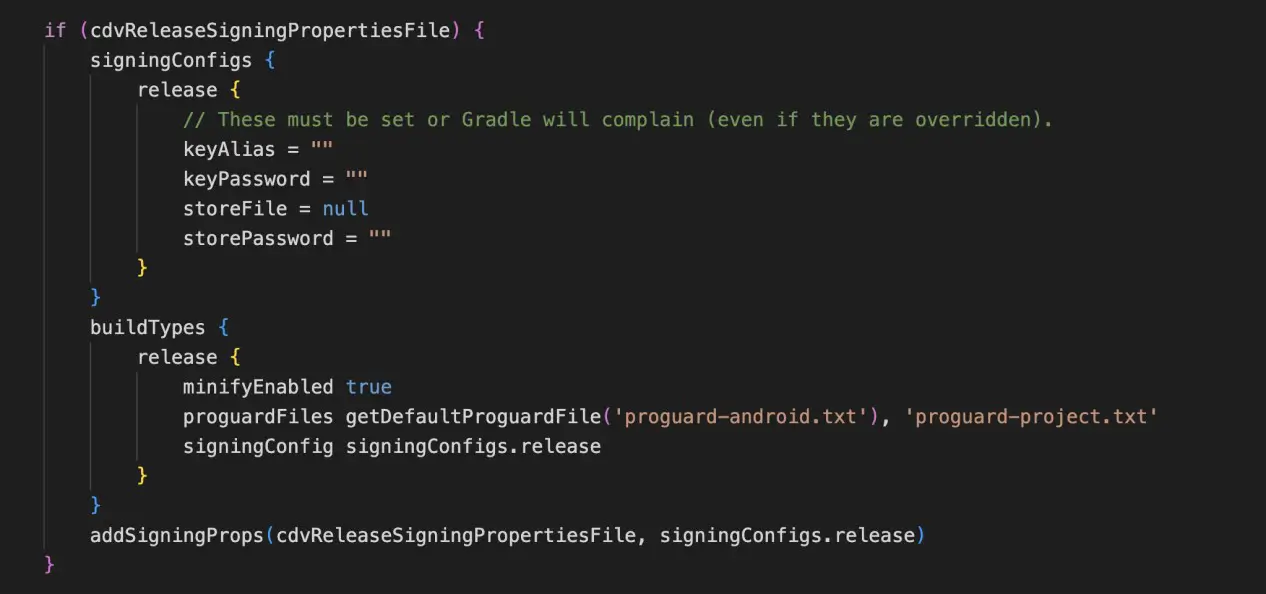
6. Then add the following lines to ‘proguard-project.txt’:
-optimizationpasses 5
-dontusemixedcaseclassnames
-dontskipnonpubliclibraryclasses
-dontpreverify
-verbose
-optimizations !code/simplification/arithmetic
-keep public class * extends android.app.Activity
-keep public class * extends android.app.Application
-keep public class * extends android.app.Service
-keep public class * extends android.content.BroadcastReceiver
-keep public class * extends android.content.ContentProvider
-keep public class * extends android.app.backup.BackupAgentHelper
-keep public class * extends android.preference.Preference
-keep public class com.android.vending.licensing.ILicensingService
7. Similarly we can add other Cordova plugins proguard rules those we are using in our application.
8. Run the following command to build your ionic app in release mode:

React Native Application
To set up ProGuard in a React Native application, you can follow these steps:
1. Open the ‘android/app/build.gradle’ file in your React Native project.
2. Find the ‘buildTypes’ block in the file. It should look something like this:

3. Change the ‘minifyEnabled’ option to ‘true to enable ProGuard:

4. Update the ‘proguardFiles option to point to the ProGuard configuration files that you want to use. By default, React Native includes the proguard-android.txt’ file, which contains some basic rules for optimizing and obfuscating your code.
5. Save the ‘build.gradle’ file.
6. Build your app in release mode to apply the ProGuard settings. You can do this by running the following command in your project directory:

That’s it! Your Android Native, IONIC & React Native app is now built with ProGuard enabled. ProGuard will optimize and obfuscate your code, making it harder for attackers to reverse engineer or tamper with.
Conclusion
These are some strategies and techniques to safeguard your app against reverse engineering, which can be exploited to extract the source code of your Android app. Utilizing tools like Proguard and other similar solutions can establish a protective shield against different cyber threats. Moreover, encryption techniques like hash algorithms should be applied to secure crucial files, making it difficult to decipher the source code. Employing these Android reverse engineering protection tips can add an additional layer of security to your app.
At OdiTek, our skilled team of developers can bring your app ideas to life with custom solutions tailored to your specific needs. Contact us today to learn more about our services and how we can help you achieve your mobile app goals.