WebRTC is a real-time communication platform that facilitates audio calling, video conferencing, instant messaging, etc. WebRTC doesn’t require any additional plug-ins or a third party to establish the connection among two browsers. While establishing the connection certain VPNs are used which may cause you severe problems such as security threat and personal data loss.
To keep your data safe and secure you can take certain security measures with the help of WebRTC Security. Do you have any idea about WebRTC security? What is WebRTC and how it works? What are WebRTC alternatives? The following post will help you with these queries.
Introduction: WebRTC provides highly secured data transmission with the help of security obligations. However, the developers can improvise the three sets of APIs such as getUserMedia, RTCPeerConnection, RTCDataChannel to modify the data transfer operations more securely. WebRTC has such a higher level of security obligations that it ensures the data are protected with end-to-end encryption. Such things help users to protect their private data from unwanted intrusions. WebRTC Security protects users from malicious parties and safeguards their data as soon as they are entered into the systems.
WebRTC Security
While using real-time communications platforms there could be scenarios that will compromise user security as well as privacy. When it comes to WebRTC, it has plenty of native built-in features that solve these security issues immediately. Usually, plug-in features give an invitation to malware but WebRTC doesn’t require any additional plug-ins so there is no chance of such issues.
The real-time communication is facilitated by certain underlying components that run in the browser’s sandbox are updated regularly and automatically when the browser is updated. Apart from this while WebRTC application uses a microphone or camera, there will be an active indicator displayed by the browser, WebRTC security ensures that the camera and microphone operation is end-to-end encrypted.
Foundation of WebRTC Security
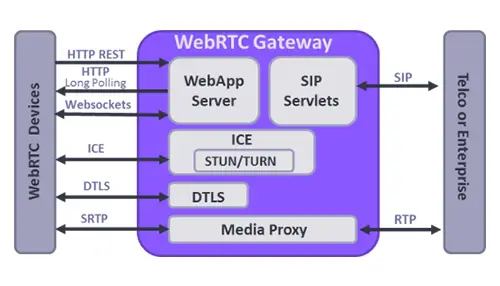
While using real-time communication the data such as camera, microphone, text, etc. must be encrypted through the DTLS or Datagram Transport Layer Security method. DTLS is a standardized protocol defined by RFCs 6347, 5238, 6083, 5764. It is there in-built in all browsers supporting WebRTC. DTLS method is originated in such a way that it will prevent the browsers from information tampering. This entire method was imitated from Transport Layer Security or TLS protocol that provides complete encryption in addition to data confidentiality, asymmetric cryptography, and text authentication.
It is usually used in email, web browsers and, VoIP platforms for encryption purposes. WebRTC Security provides end-to-end encryption regardless of any server. It ensures the WebRTC media data can be secured through any standard SSL based connection. Let’s take, for example, a TURN server that can resolve the UDP layer of a WebRTC packet. Apart from this the data can neither be modified nor understood by the server. Simply we can say that the servers couldn’t decode the fragile data that is transferred between peers.
The media as well as the signaling layers can be encrypted through certain mechanisms depending upon the signaling layer selected. Certain communication platforms use TLS to encrypt their Web Sockets or any kind of web traffics. The Signaling layer helps to detect the user’s identity through the authentication mechanism. Let’s take for instance users while using SIP put some unique user names and passwords to ensure their identity. This can also limit the number of persons who can call you. Apart from passwords, other identity frameworks like OpenID, OAuth, or Persona can also be used for the same operation.
WebRTC Security Measures
The WebRTC Security measures are divided into 3 major groups such as-
1. Server Security: WebRTC is an end-to-end communication channel that works under a particular server. Pre-WebRTC Security software components such as STUN and Identity Provider (IdP) implement the security measures performed by the server. IdP is used to authenticate the identity of the party whereas STUN is used to identify the external network address.
2. Client Security: To carry out the basic functionalities such as video communication, direct data transfer, P2P audio communication, etc. major browsers are used. There are two types of architectures that are adopted by the browsers for authorization such as-
a. While usage, media device permissions are required
b. When a media device is in use, the users are informed about it.
These things are done to maintain transparency between users and browsers. We can take a simple example to understand this – While going for a video conference, the microphone and video camera access are required for which WebRTC will ask for your authorization.
3. Communication Channel security: Communication channel is the pivotal part of WebRTC. WebRTC has a particular specification that forbids the corrupted or pirated browsers to access the RTC platform. It only allows the secured as well as the encrypted version for operating. It ensures both the signaling plane as well as the media plane are secured and protected which is a difficult task. Hence to solve this issue DTLS-SRTP protocol came into the picture. Since TLS is an expensive operation to be adopted, SRTP can be used in place of TLS for lightweight encryption.
An attacker can listen to your conversation with the help of the MitM attack if the communication process is compromised between two peers. To protect this you can take the help of standard TLS certificate exchange. Here both the parties interchange the self-attested TLS certificates between each other. The TLS certificate is initially sent by the signaling channel and then via media channel. Now forging the certificate will require SSL encryption to the signaling server, which is almost impossible to conduct so that you no more have to face such attacks further.
WebRTC Alternatives
WebRTC is a beautifully designed technology that is functioning successfully in this digital world. It has a high potentiality in terms of security and privacy policy. If you are talking about WebRTC alternatives then there are wide varieties of alternatives to WebRTC are available such as-
1. Zoom: It provides cloud video conferencing, online meetings, group chat across different platforms, etc.
2. Twilio: It offers a powerful API to developers for making and receiving calls through phone services.
3. Google Meet: It is the business-oriented version of the platform Google’s Hangout, which is suitable for all sizes of business.
4. Skype: It provides flawless text, video, and voice communications to facilitate simple sharing experience.
5. XMPP: It is a set of open technologies available for instant messaging, multi-party chat, voice as well as video calls.
6. Discord: It is a modern technology which enables gamers to communicate among each other through voice and text chat platform.
New Possibility with WebRTC Security
WebRTC Security provides powerful APIs which enable the developers to build real-time communication without any additional plug-ins. There are certain built-in operations in Chrome, Opera, and Firefox browsers such as high definition video as well as voice transfer along with powerful encryption of DTLS. The amplification of voice and video streaming represents some new opportunities in the province of WebRTC Security.
WebRTC security issues are resolved by the new models of security provided by WebRTC through the developers which will help in keeping the data more secure and encrypted. When your business will be merged with the powerful security methods provided by OdiTek Solutions, you can discover an ascendable application that will help you connect your business globally.
CONCLUSION
It is a very complicated task to understand the security issues of any specific technology. Though WebRTC is a properly designed technology, yet it faces security threats some times. WebRTC Security protects the peer’s data from any kind of security threat through its strong architecture. But if any further threat outbreaks crossing the security then Proper alleviation techniques should be adopted for the threats as soon as they appear. OdiTek Solutions provide you with developed signaling infrastructure that is already serving many small and medium-sized businesses. It has specially designed geographically distributed SIP proxies that will help the developers to connect with their peers beyond Firewalls and NAT to bridge the gap between the two browsers.